Blog
Understanding End-to-End Encryption for Photo Storage
Photos feel personal. They capture family times, houses, and everyday life. Most people upload them without much thought because apps say photos are encrypted. That word creates a sense of safety, even when users do not know what it truly means.
The real issue is not where photos are stored. It is who controls access to them. End-to-end encryption is meant to protect photos by limiting who can unlock them. This article explains what that protection really covers and where privacy can still be breached. Let’s get started!
Why Photos Need More Protection
Photos are more than simple files. They capture moments people never expect to share beyond a small circle. That makes them far more sensitive than most digital data.
A photo can reveal more than a message.
One image can show:
- Faces
- Locations
- Homes
- Daily routines
If a photo is exposed, you cannot undo it. You cannot take it back. That is why photos need stronger protection than basic files. It is meant to offer that protection, but only when it is used correctly.
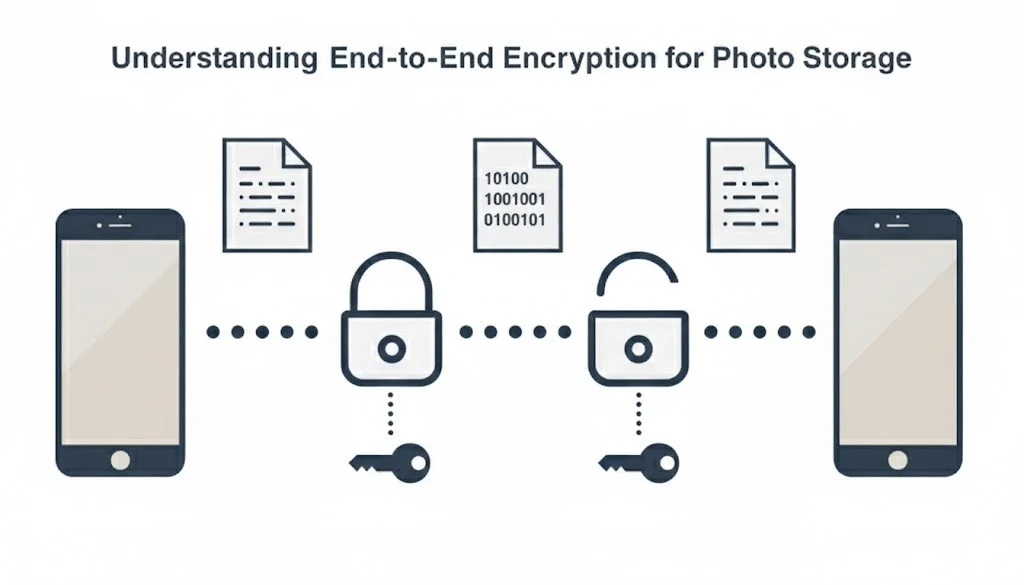
What End-to-End Encryption Means in Simple Terms
End-to-end encryption is concerned with access but not storage. It determines who is authorized to open a photo and who does not have such powers. It is to indicate that your photo is locked before it flies out of your phone.
Only the individual to whom you are sending it can unlock it.
The service moving the photo:
- Cannot open it
- Cannot read it
- Cannot scan it
The encryption key stays with the user. It never reaches the service. In the event a platform is able to decrypt your photos to offer assistance or recovery, then it is not end-to-end encryption.
How the Process Works
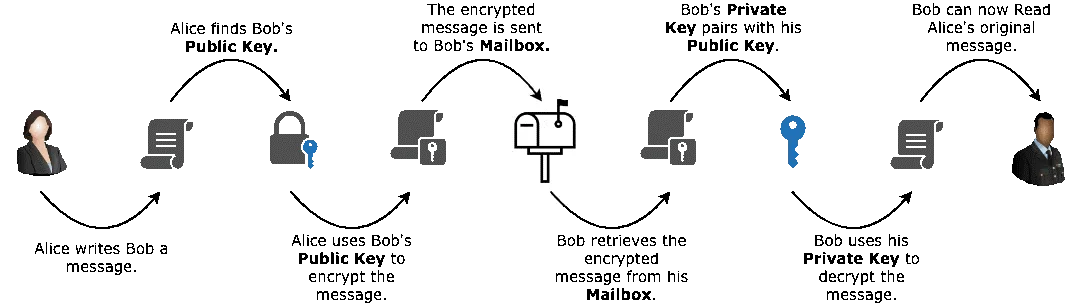
The concept of end-to-end encryption is easy, as it can be divided into steps. Each step limits access at a different point.
Here is the basic flow.
- Your device locks the photo
- The locked photo travels through servers
- The receiver’s device unlocks it
The servers act like a delivery truck. They move the package but cannot open it. This setup protects photos even if servers are compromised.
Photos Are Not Like Text Messages
Photos behave differently from text, both in size and in content. They often hold more personal details in a single file. Photos are larger and more complex than text.
They often include:
- Image data
- File structure
- Extra hidden details
With proper end-to-end encryption:
- The photo content stays private
- The service cannot view the image
- The file stays unreadable during transfer
If encryption starts only after upload, the provider still has access at some point. That gap matters.
What Is Protected and What Is Not
Encryption offers some level of protection to a part of a photo, but not all aspects attached to it. Understanding the difference is a way of having realistic expectations.
This includes:
- The image
- The visible details
Some basic information may still exist to keep systems working.
This often includes:
- File size
- Time sent
- Sender and receiver
This information is called metadata.
Metadata can still reveal patterns, even when the photo itself stays private. That is why encryption improves privacy but does not eliminate all signals.
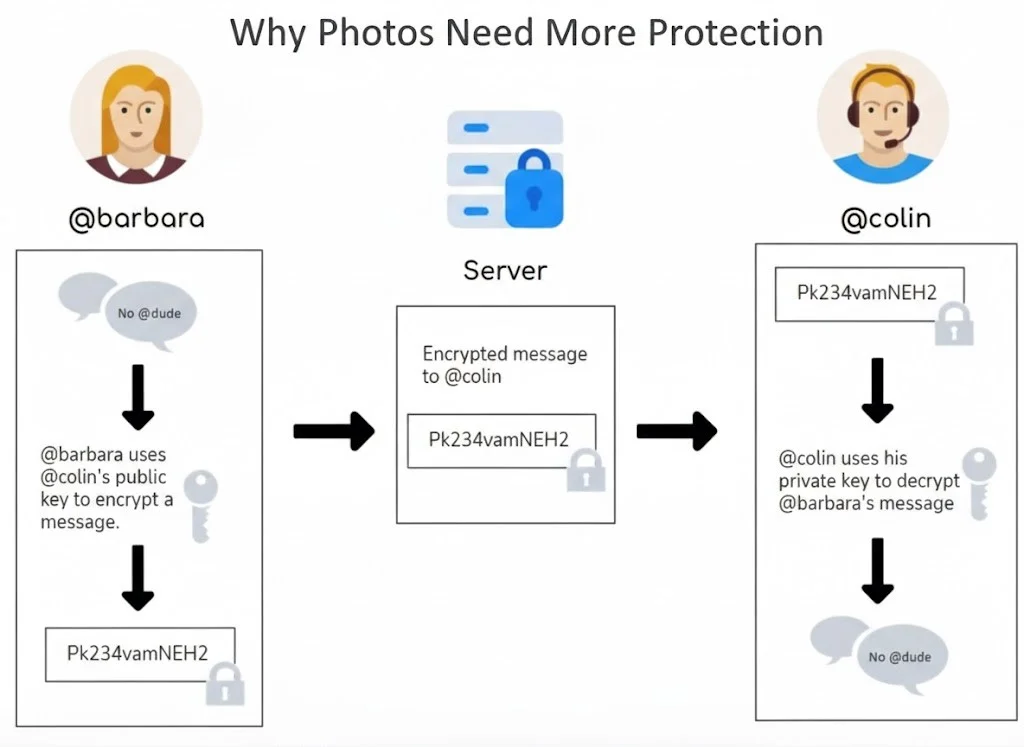
The Key Question: Who Holds the Key
Many platforms use the word encryption in their marketing. Far fewer explain who actually controls access behind the scenes. Many services advertise encryption. Fewer explain who controls it.
There are three common setups.
Transport protection
Data is protected while moving.
Servers can still read it.
Server protection
Data is protected on servers.
Providers keep the keys.
End-to-end encryption
Data security is ensured at all levels.
Users keep the keys.
If a service can recover your photos without your involvement, it likely controls the keys.
Technology researcher Matthew Green explains it simply:
“Security fails when users are told they have privacy but do not have control.”
For photos, control comes from key ownership.
Photos on Devices and Photos in the Cloud
Where a photo is stored changes how much control you have over it. Device storage and cloud storage follow very different rules. Photos stored only on your phone rely on device security.
This includes:
- Screen locks
- Biometric access
- System protections
Once photos move to the cloud, the rules change.
Cloud services may:
- Store multiple copies
- Enable recovery tools
- Allow account-level access
Some sites will minimize this risk by encrypting images before uploading and retaining keys with the user. This approach is often used in privacy-focused cloud storage for photos, where provider access is limited by design.
Backups and Long-Term Privacy
Backups are meant to protect against loss, but they can quietly change who has access to your photos over time. Backups prevent loss. They also affect privacy.
Many backups:
- Encrypt photos
- Keep recovery access
- Allow provider involvement
Some systems offer encrypted backups that require a recovery key. If that key is lost, the photos cannot be restored.
This creates a trade-off between convenience and responsibility. Users should know which option they are choosing.
Sharing Photos Safely
Sending a photo securely is only one part of privacy. The post-delivery is equally important. End-to-end encryption secures the photos as they are being transmitted. It does not dictate the future of it.
Once a photo is:
- Saved
- Forwarded
- Captured in a screenshot
Encryption no longer applies. This matters for parents, professionals, and anyone sharing sensitive images.
What End-to-End Encryption Cannot Stop
Even the strongest encryption has limits. It cannot protect against every possible risk. Even strong encryption has limits.
It does not protect against:
- Someone unlocking your phone
- Malicious apps
- Copies saved outside secure apps
Most privacy issues come from device access, not broken encryption. Good security combines encryption with smart habits.
Common Misbeliefs About Photo Encryption
Many people trust encryption without understanding how it works. This leads to false confidence.
Common beliefs include:
- Encryption hides everything
- Providers cannot access content
- Backups are always safe
These assumptions are incomplete.
Encryption protects data. Control depends on system design. Understanding that difference prevents false confidence.
Why This Knowledge Matters
Photos are records of real life. They capture growth, work, and private spaces that cannot be replaced. Photos document real life. Children are growing up. Work projects. Private spaces. Most photo privacy problems start with unclear choices, not attacks.
People who understand end-to-end encryption:
- Ask better questions
- Review settings carefully
- Choose platforms with intent
That awareness prevents problems before they appear.
Conclusion
End-to-end encryption is not about technical terms. It is about ownership. If you control the keys, you control access to your photos. If you do not, someone else may. After reviewing how different photo systems work, one lesson stands out. Privacy fails quietly, long before users notice.
Clear knowledge helps prevent that failure. When people understand how photos are encrypted and who holds control, they protect their memories with purpose instead of assumption.